by Swapneela Unkule
NIST SP 800-56A provides recommendations for Pair-Wise Key-Establishment Schemes Using Discrete Logarithm Cryptography. Diffie-Hellman (DH), Elliptic Curve DH (ECDH) and Menezes-Qu-Vanstone (MQV) key-agreement schemes are specified in this standard. These Key-Agreement Schemes (KAS) are widely used in network protocols such as TLS.
The SP 800-56A has been revised twice since its initial publication in January 2007. SP 800-56A Rev2 was published in May 2013 to allow the use of additional key derivation functions (KDF) documented in SP 800-135 and SP 800-56C. SP 800-56A Rev3 was published in April 2018, which introduced “safe-prime” groups and moved all of the key derivation functions to SP 800-56C.
The Cryptographic Module Validation Program (CMVP) have been encouraging the vendors to implement SP 800-56A compliant key-agreement schemes, but have not yet mandated the compliance. The long standing FIPS 140-2 Implementation Guidance (IG) D.8 permits six (6) different scenarios of key agreement, ranging from a fully SP800-56A compliant KAS, to a compliant component such as Shared Secret Computation (SSC) or KDF, or a totally non-compliant key agreement method. The CMVP have been generously allowing the use of all methods as described in the six scenarios in the FIPS mode of operation. It has been in discussion for years that this would change at a certain point. The questions of when to change and how to change have been the topic for the Cryptographic Security Testing (CST) lab managers’ meeting for years.
On August 12, the IG D.8 was updated with the transition plan to SP 800-56A Rev3. The recent CST lab managers’ meeting on August 26 confirmed the enforcement of SP 800-56A Rev3 compliance. The CMVP finally pulled the trigger to tighten up this loose end by a two-phase approach.
Starting January 1st 2021, all new and updated FIPS submissions will need to be NIST SP 800-56A Rev3 compliant, if KAS or SSC is claimed in the FIPS approved mode. Vendors will have one year to address the SP 800-56Ar3 compliance requirement for already validated FIPS modules. Vendors may update the module’s Security Policy by removing any claim about KAS or SSC from the FIPS approved mode, or get the required CAVP certificate(s) for KAS, SSC and KDF and add required self-tests. Please see the table at the end of this article for the summary of the required CAVP certificate(s) and self-tests in details. Note that submissions under FIPS 140-2 are only allowed up to September 2021.
On July 1st 2022, validated modules affected by IG D.8 that have not been updated to either reflect the SP 800-56Ar3 compliance or to remove all the claims of compliance to earlier versions of SP 800-56A in the FIPS approved mode, will be moved to the Historical List. Being listed on the Historical List implies that “the referenced cryptographic module should not be included by Federal Agencies in new procurements. Agencies may make a risk determination on whether to continue using this module based on their own assessment of where and how it is used.”
FIPS 140-2 IG D.8 specifies two scenarios (X1 and X2) that can be claimed as approved key agreement methods past December 31st 2021, apart from the RSA based key agreement scheme. Scenario X1 includes compliance to SP 800-56A Rev3 either by implementing just the shared secret computation or the complete key agreement scheme. Scenario X2 corresponds to the use of the ECC scheme based on non-NIST-recommended Elliptic Curves.
The new revision of IG D.8, published on August 12th 2020, requires self-tests of the underlying security functions and the appropriate assurances, as required in section 5.6.2 of SP 800-56Ar3 as shown in the table below. The CAVP testing for SP 800-56A Rev3 SSC and KDF is currently available. The testing for the complete KAS is planned to be available by the end of September.
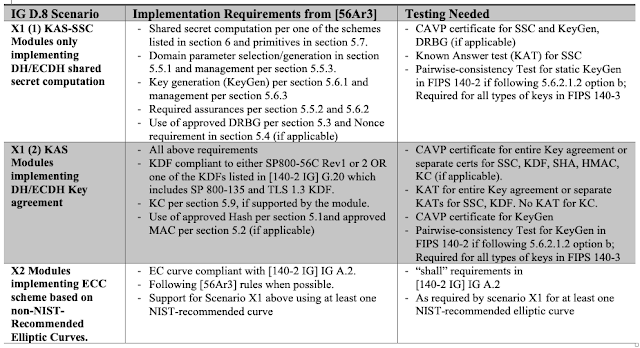
FIPS 140-3 Annex D (NIST SP 800-140D) only recognizes SP 800-56A Rev3 as the standard for FIPS approved and NIST recommended Key-Establishment Schemes Using Discrete Logarithm (i.e. Key Agreement Schemes). FIPS 140-2 D.8 will be carried over to FIPS 140-3 IG as D.F Key Agreement Methods.
We urge vendors to start implementing the SP 800-56A Rev3 compliant KAS and the required self-tests in IG D.8 as soon as possible if they need KAS to be used in the FIPS mode.
For the details of the differences between different revisions of SP 800-56A, please read this white paper.
References:



