-

ICMC and Dr. Bertrand du Castel
Sal La Pietra, the President and co-founder of atsec information security (atsec), opened the tenth annual International Cryptographic Module Conference this morning at Westin Arlington Gateway in the Washington D.C. area.
-

Securing the Software Supply Chain
All components comprising a software product are ultimately the responsibility of the developer of that product, even if one or more of those components is supplied by a third party. This is especially true when the product is evaluated for Common Criteria (CC) certification. Recently, the National Security…
-

Challenges and Opportunities
Many of us who have been in the evaluation and certification (validation) business have seen the development, not only of security requirements and schemes, but also how the “security echo system” works. A few weeks ago, I was generously given the opportunity to share some ideas at the…
-
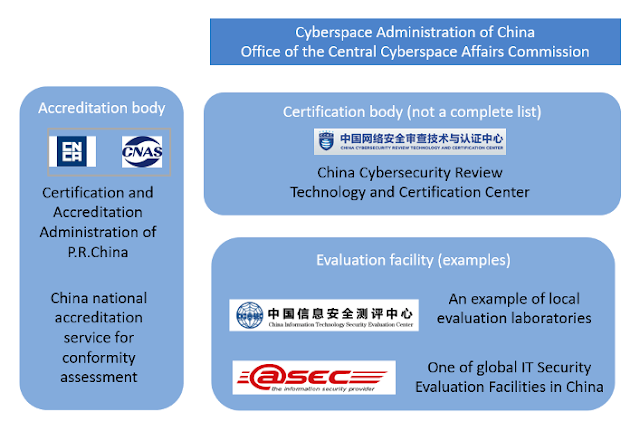
Update on the IT Security Standards in China
(“Information Security and Cryptography” in Chinese Calligraphy) In this article, we provide an up-to-date overview regarding IT security standards as well as the current situation of IT security testing and certification in China. It also covers the topics related to security assessment and compliance in the financial industry.…
-

Quality and Security – more than just words
At atsec, quality and security are more than just words – they encompass everything we do and are deeply embedded in our four principles: We know the businessWe act with integrityWe stay focusedWe are independent Management is committed to the implementation and improvement of an integrated Management System.…
-

atsec attended the 20th International Conference on Applied Cryptography and Network Security (ACNS)
Last week, employees from atsec Germany and atsec Italy attended the 20th International Conference on Applied Cryptography and Network Security (ACNS) in Rome, Italy. As the name implies, ACNS highlights academic and industry research in the areas of applied cryptography and network security. Accepted papers are published in…
-

Cybersecurity Certification Schemes in Europe
atsec has recently participated in two conferences that focused on cybersecurity certification: the 2022 International Conference on the EU Cybersecurity Act in Brussels, Belgium, and ENISA Cybersecurity Certification Conference 2022 in Athens, Greece. atsec contributed with two presentations at the EU Cybersecurity Conference “Successful cPP Certification under the…
-

atsec attended the Omnisecure conference in Berlin
After two years of video conferences, we were finally able to meet stakeholders of our community again in person as three representatives of atsec Germany attended the Omnisecure conference from June 21st through 23rd 2022 in Berlin. The Omnisecure conference has a clear focus on the German market…
-

Distinguishing encrypted from non-encrypted data
Our colleague Quentin Gouchet, together with Eric Järpe, authored an article on distinguishing encrypted from non-encrypted data. We invite you to read the article here. Introduction:The discrimination of encrypted data from other kinds of data is of interest in many areas of application. For instance for making other…
